The New Perimeter: Protecting Edge Infrastructure with AI in a Distributed Workforce
Sep 04, 2025
Enterprise edge security has evolved far beyond the traditional ‘castle-and-moat’ approach to a model defined by layered defenses, spanning hardware firewalls, virtual firewalls, and cloud-based Secure Service Edge (SSE) solutions.
With AI-driven attacks on the rise, scalable and intelligent solutions are no longer optional, they’re essential. Leveraging AI in perimeter security as a strategic countermeasure is critical to staying ahead of these evolving threats. As cloud-native services and artificial intelligence reshape traditional defence models, organizations must rethink legacy strategies and embrace adaptive, AI-powered strategies. This blog post explores the journey from hardware firewalls to SSE and the pivotal role AI will play in shaping the future of cybersecurity.
The evolution of the perimeter
With rapid cloud adoption, workloads have moved outside corporate boundaries, creating multiple perimeters. Consequently, data traffic has shifted beyond the traditional enterprise edge. Hybrid work is now the norm, giving employees access to sensitive applications on personal devices regardless of location. The modern perimeter hence spans branches, remote workers, IoT/OT environments, public and private clouds, and business partners. This complexity makes it clear that the conventional one-size-fits-all approach no longer works. The question is: Which approach is best for securing this dynamic environment? Should enterprises rely on next-generation firewall (NGFW) appliances or adopt cloud security services like SSE? And more importantly, how can enterprise edge security scale to meet the needs of distributed workforces?Why SSE matters today
Reflecting on the evolution of enterprise security, it’s remarkable to consider how far we’ve come since cloud proxies and security services first emerged in 2008—a time when terms like Secure Service Edge (SSE) hadn’t even entered the conversation. . Today, the SSE market is thriving, with numerous established vendors offering centralized security management and rapid provisioning. For most enterprise edge locations, traditional hardware firewalls are no longer necessary. In fact, SSE enables faster deployment, stronger service-level agreements, and reduced administrative overhead for security teams. For businesses founded in the last decade, SSE has consistently been the preferred approach. The pandemic further accelerated this transformation. As organizations transitioned to remote work, SSE became a critical enabler, ensuring secure connectivity and uninterrupted business operations. But the lingering question is: Will SSE alone be enough to future-proof enterprise edge security?The era of distributed firewall functions
If SSE is so effective, why do hardware firewalls still exist? They remain essential for enterprises with on-premises data centers, securing east–west traffic, VPN termination, or when cloud security introduces unacceptable latency. Looking ahead, the firewall will evolve beyond its traditional definition as a hardware appliance or Firewall-as-a-Service (FWaaS). It will become a distributed function across the network, decoupled from any single appliance or SSE solution. As attack surfaces expand, organizations will adopt distributed firewall architectures with centralized policy engines and diverse enforcement points which could be hardware appliances, virtual appliances, and cloud services. You won’t find a silver bullet solution for enforcement points. However, there will be a shift towards consolidation in policy administration through centralized policy engines. This approach will simplify provisioning and streamline management across various enforcement points, effectively protecting multiple perimeters.AI: The game-changer in cybersecurity
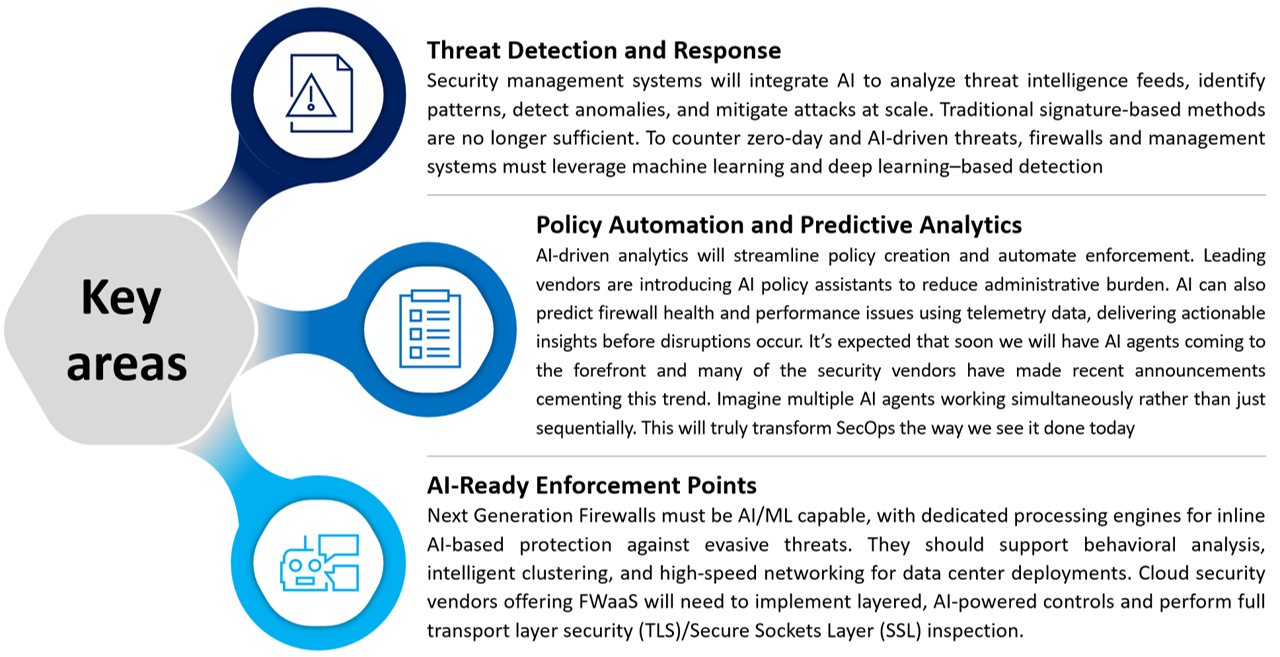
With great power comes great responsibility. As perimeter defense systems monitor and learn more, AI will become indispensable in enabling automation, agility, and predictive security.Key areas where AI will transform security

Building an adaptive security future
As organizations adopt AI-driven security, adversaries will do the same, making attacks more sophisticated and harder to detect. This arms race demands that defenders stay ahead with intelligent tools. Enterprises should fully leverage AI for real-time threat detection, risk assessment, and rapid response. Embedding AI into security architecture enables automation, fast data analysis, and predictive modeling to anticipate and counter threats before they materialize. The future of cybersecurity lies in adaptive, intelligent layers that continuously learn and improve, guided by human expertise. Success will belong to those who combine innovation, automation, and human insight in a balanced way. The era of passive defense is over—now is the time to build smart, proactive security for the new perimeter.References
- Detecting Zero-days with SnortML Whitepaper, CISCO, August 20, 2024: https://www.cisco.com/c/en/us/products/collateral/security/firewalls/detecting-zero-days-with-snortml-wp.html
- The Multi-Agent System: A New Era for SecOps, TORQ, May 28, 2025: https://torq.io/blog/the-multi-agent-system-a-new-era-for-secops/
- Requirements for Preventing Evasive Threats: Incorporating Deep Learning, Comprehensive Coverage, and Intelligent Management into Network Security, Palo Alto, March 25, 2022: https://www.paloaltonetworks.com/resources/whitepapers/esg-requirements-for-preventing-evasive-threats
